Connected Apps is a feature provided in Anypoint Platform under Access Management. Connected Apps can help
the developers to use the standard OAuth 2.0 and OpenID Connect protocols to authenticate users, provide
single sign-on, and issue tokens to use with Anypoint Platform APIs with granular control over specific
tasks which an app can perform by defining the scopes for the apps. Anypoint Platform users, on the other
hand, can leverage a set of additional access controls to safely share their account data with third-party
applications to perform certain tasks on their behalf.
Types of Connected Apps and Use Cases
Connected Apps can be classified as either first-party apps (on behalf of the app itself) or third-party apps
(on behalf of the users), based on the ownership of the application. The key difference refers to who has
administrative access to the Anypoint Platform domain.
- First-party applications are designed for server-to-server
applications. These are controlled by the same organization or person that owns the domain.
These apps can simplify your existing workflows, e.g., CI/CD pipeline or any other utility built by your
organization to access and manage the Anypoint Platform programmatically. When using a connected app to
perform a certain task(s), one does not need to create a separate service user but only needs to create
a connected app that can securely connect to the platform to perform those tasks.
- Third-party applications are generally controlled by different people or organizations
that might not have administrative access to an organization’s domain. These apps enable
third-parties, such as partners, developers, vendors, etc., to securely access protected resources of an
organization. It can help the third-parties to provide single sign-on capabilities for
an enhanced and more cohesive user experience for authenticating applications using the Anypoint
Platform. Thus, it can be used by the applications that consume the Anypoint Platform data and provide
functionality based upon that data such as dashboards, performance metrics, centralized infrastructure
control, etc.
Connected Apps’ Creation and Usage
To create a Connected App, a user requires access to ‘Access Management’ (admin access to the
master organization) in the Anypoint Platform. Below are the steps to create a connected app:
- Login to the Anypoint Platform with the user having the appropriate access.
- Navigate to Access Management on the left side menu. The option for ‘Connected
Apps’ appears under Access Management, as shown in the figure given below.
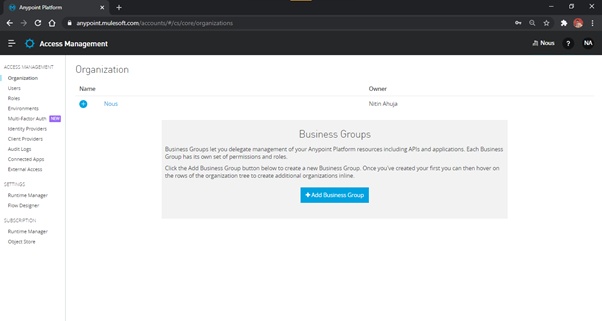
Fig-1 : Access Management
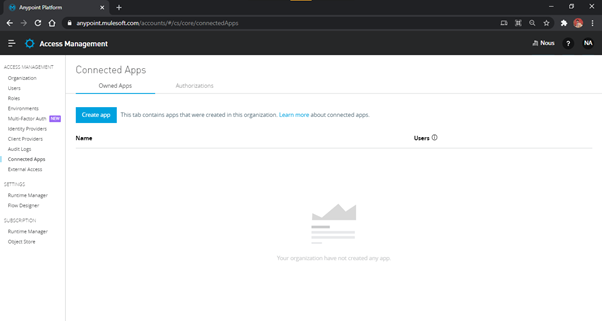
Fig-2 : Connected Apps
- Click the button labelled ‘Create App’ to create the Connected App. A page with the
application details opens, as shown in Fig. 3.
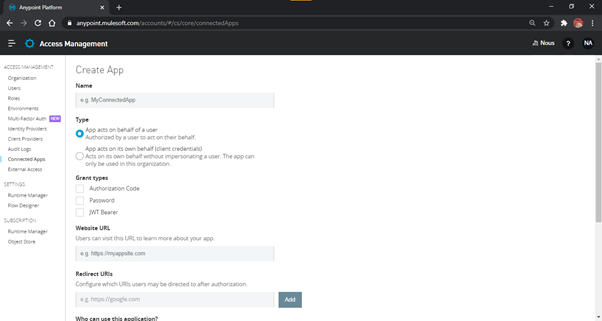
Fig-3 : Connected App Creation
Based on the type of app, follow the steps as given below:
First-party (On Behalf of Itself)
A first party app that acts on its own behalf can be created by selecting the option ‘App acts
on its own behalf (client credentials)’. This takes the app name and scopes to generate
the client credentials – client_id and client_secret.
NOTE: Provide the appropriate scopes while saving the API, else it may result in an
unauthorized error when the APIs are hit with the token generated for this app that does not have the scope
for that API/functionality. The following figure displays the scopes to access the API Manager.
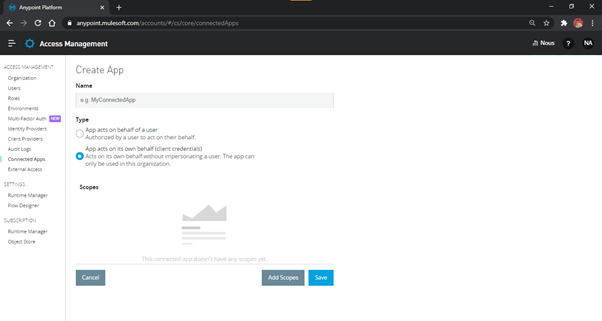
Fig-4 : FirstPartyApp - Create App Page
- After providing the name of the app and the scopes as shown in Fig. 5, click ‘Save’. The
created app appears in the Connected Apps page. Copy the client_id and client_secret as shown in Fig. 6.
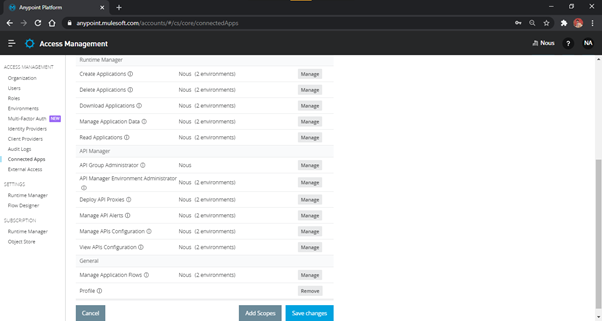
Fig-5 : FirstPartyApp - Scopes
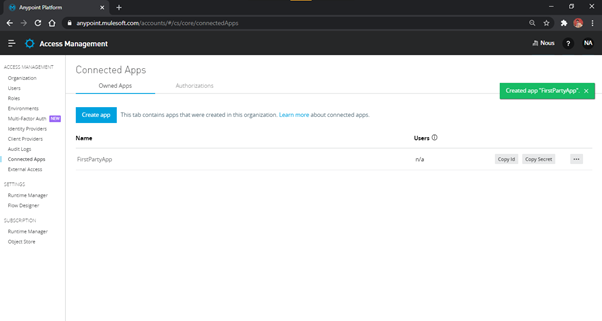
Fig-6 : FirstPartyApp - Created
- Create a request in Postman (or any other rest client), as shown in Fig. 6, to generate a token using
the client_id and client_secret provided by the Connected App created in the above steps.
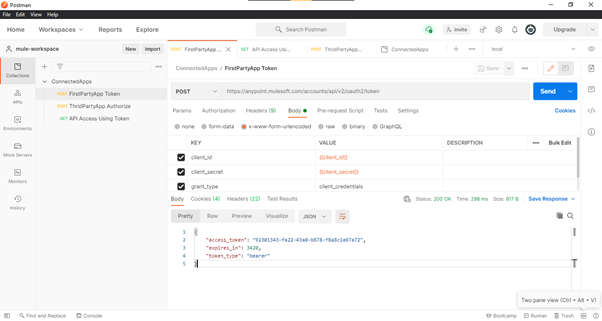
Fig-7 : FirstPartyApp - Token Generation
- The retrieved access token can be used to call any Anypoint Platform API. Here, we have hit an API
Manager endpoint to show the API in a specific environment of a specific organization.
NOTE: Here, organization id and environment id are copied into the environment variables of
Postman from the Anypoint Platform as shown in Fig. 8.
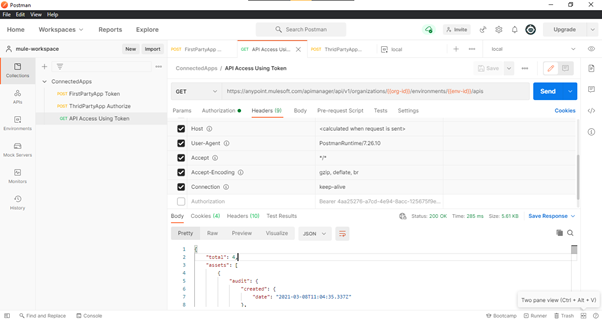
Fig-8 : API Manager’s APIs endpoint result using FirstPartyApp Access Token
Third Party (On Behalf of the User)
- To create a Third Party App, select the option ‘App acts on behalf of a user’ from the
create Connected Apps page along with Grant Types, Redirect URI, and Scopes as shown in Fig. 9 and Fig.
10.
NOTE: We have selected Authorization Code along with Refresh Token, but you can use any
other or all the available options as well. We have also given a Redirect URI for the Postman app - Callback, which
can return the auth code back to Postman when initiating from there. You may provide your own appropriate
URI(s) and multiple URIs as well. When you initiate the request for auth code on/authorize
endpoint, it will require you to pass the Redirect URI as well, which will be matched against this list in
the App. If the URI does not match completely, you will receive ‘Unauthorized’ error. We have
provided the ‘full’ scope for full access for demonstration. You can give
a limited scope for the task that is supposed to be performed by the App.
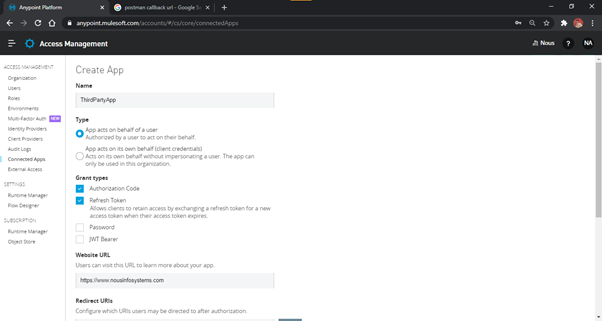
Fig-9 : ThirdPartyApp - Creation
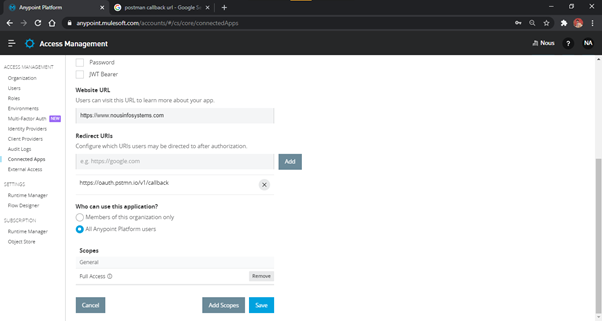
Fig-10 : ThirdPartApp - Redirect URL and Scopes
- On clicking save, after providing the appropriate details, the app is created as shown in Fig. 11.
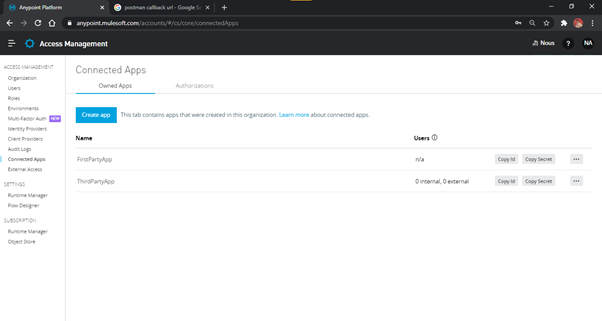
Fig-11 : ThirdPartyApp - Created
- Copy the client_id and client_secret of the app from the Anypoint Platform and use that to generate the
auth code as shown in Fig. 12. The auth code is returned after authorization to the Redirect URI within
the ‘code’ query parameter as shown in Fig. 15.
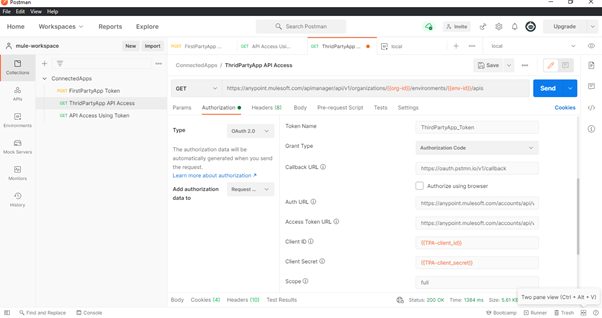
Fig-12 : ThirdPartyApp - OAuth 2.0 Authorization Code Generation
- Once you hit the generate token in the Authorization tab, you will be directed to the login page of the
Anypoint Platform as shown in the Fig. 13.
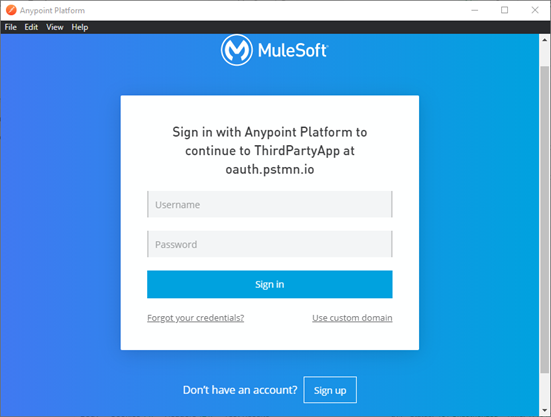
Fig-13 : ThirdPartyApp - Authorization Sign Up
- Login with your credentials to the Anypoint Platform. You will be directed to the authorization prompt
of the app, where it shows which app will receive what kind of authorization once you grant access, as
shown in Fig. 14.
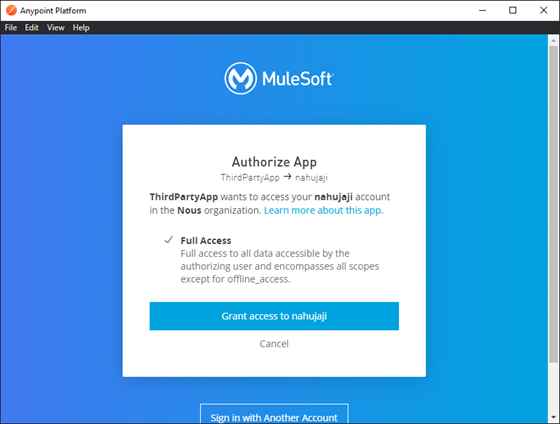
Fig-14 : ThirdPartyApp - Authorization Prompt
- Anypoint Platform will redirect you to the Redirect URI with Auth Code in the ‘code’ query
parameter, once the access is granted, as shown in Fig. 16. If you are using Postman’s authorize
flow, it will hit the / token endpoint with the auth code to generate the Access Token,
as shown in Fig.
14. You can also hit the token endpoint yourself with the Auth Code to generate the Access Token as
shown in Fig. 16.
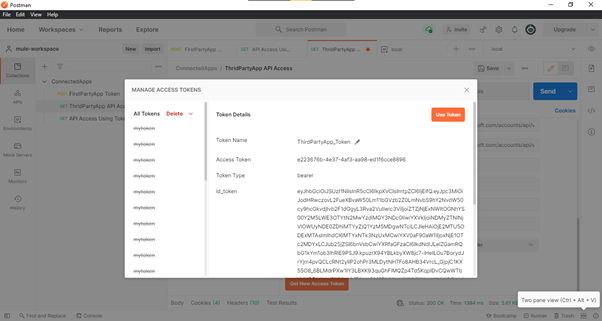
Fig-15 : ThirdPartyApp - Access Token Generated using Auth Code within Postman OAuth 2.0
Workflow
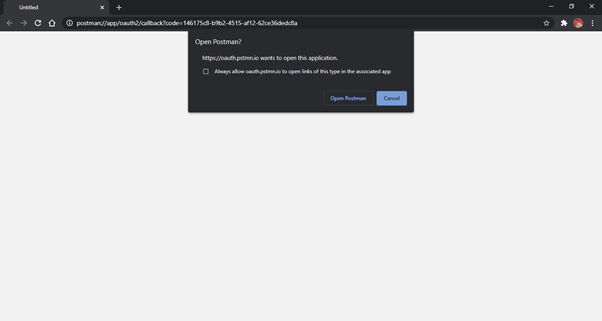
Fig-16 : ThirdPartyApp - Authorization Using Browser
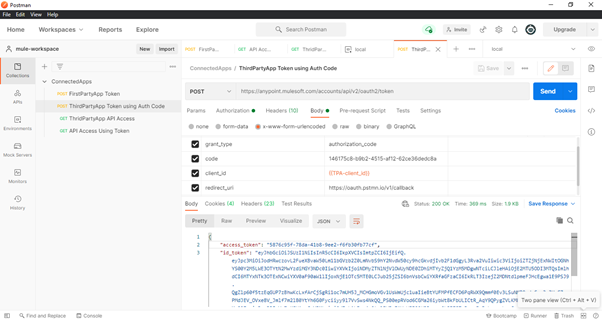
Fig-17 : ThirdPartyApp Access Token Generation using Auth Code
- Once the token is generated, it can be used to hit the CloudHub APIs within the scope of the token.
Here, we have hit the API Managers’ APIs endpoint. If the valid token with the appropriate scope
is used, then the API should respond with the success response as shown in Fig. 18.
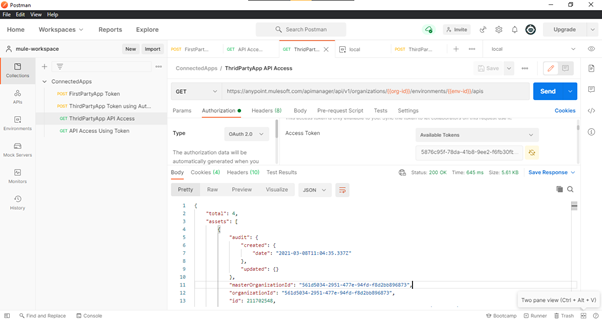
Fig-18 : API Manager’s APIs endpoint response using ThirdPartyApp Access Token
Summary
Connected Apps can be used to connect with the Anypoint Platform APIs using access tokens, which can have
limited scope(s) depending on each individual Connected App. These tokens can be generated by the apps,
either on their own behalf or on a user’s behalf using the OAuth 2.0 Authorization workflow. Using
Connected Apps, we can easily automate workflows, without requiring service users. It also provides
countless features to the platform users along with single sign-on via third party apps.
Connected Apps can provide the following benefits over creating a service user:
- Connected Apps are auditable and usage tracked
- Anytime control on access revocations
- No password changes for revoking the granted access
- Passwords can be changed without having to update other systems, as it uses the access tokens to connect
to the platform and not the user passwords